7 Ways to Improve Your Vulnerability and Configuration Management Program
IT modernization is an unstoppable force driving innovation and growth, but it’s also introducing endpoint complexity that CISOs struggle to master
IT modernization is the unstoppable force driving innovation and growth for global organizations. Unfortunately, it’s also introducing endpoint complexity that CISOs struggle to break down. Mass work-from-home orders in 2020 compounded the challenge. As the world stayed home, there was an explosion in new and unmanaged IT assets coming online.
Threat actors are getting better at finding these weak links, exploiting vulnerabilities and misconfigurations before security and IT ops teams even know that they’re there. Regulatory pressure is turning the heat up on organizations already struggling to manage the reputational and financial fallout of breaches.
At the heart of any good cyber risk management strategy lies vulnerability and configuration management. While details can vary, the vulnerability management lifecycle broadly follows the following stages:
Discover what assets you have and what security protocols are in place.
Assess what types of security and vulnerability standards you want to evaluate against, and deploy tools to figure out how to collect relevant information.
Prioritize to categorize the importance of items you want to address and how soon they should be tackled.
Remediate to address vulnerabilities by updating patches and changing security configurations and policies.
Verify/reassess to close the loop by validating that the changes you’ve made have conformed to security policies.
But this broad framework provides plenty of scope for improvements to be made. Here are seven ways you could enhance your program to help minimize cyber risk in the endpoint environment.
1. Prioritization is key
The exponential growth in enterprise endpoints makes it impossible to fix all issues you might find straightaway. That makes effective prioritization a key activity. First, it’s about prioritizing or determining the criticality of your IT assets — whether they’re laptops, servers, virtual machines, containers or other endpoint types. A production database server is likely to be more valuable to the organization than one sitting in the development environment, for example. This work can be slotted in between the Discover and Assess phases of the lifecycle.
Then, use the results from your assessment stage to prioritize actions based on the criticality of both assets and the vulnerability/configuration issues that affect them. Continuous visibility and monitoring should be your watchwords here.
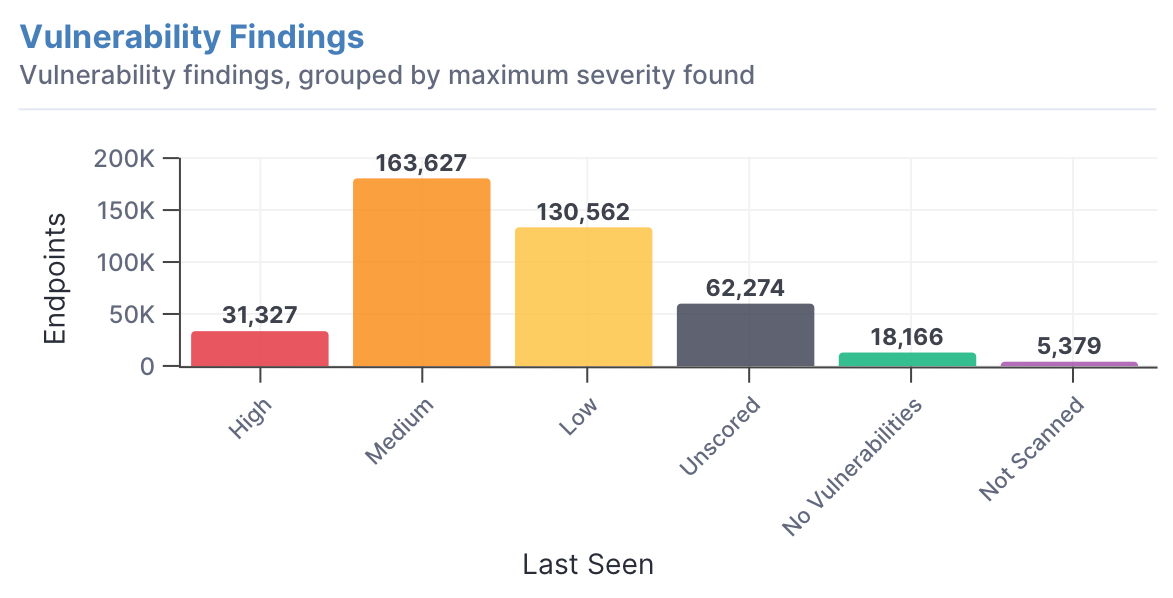
Vulnerability data based on severity
2. Focus on remediation
Prompt remediation of vulnerabilities and configuration issues is essential, as attackers act quickly and continue to get better at exploiting security gaps once identified. While many security teams perform frequent scans and have good situational awareness of where these weak points are, fixing them is another matter. There’s a commonly held view that throwing people at the problem is the answer. But in reality, even large IT teams can become quickly overwhelmed by the sheer number of issues and endpoints in need of remediation.
While prioritization is vital, automation keeps the lifecycle loop flowing smoothly. For teams worried about automated patches breaking critical systems, secondary evaluation processes can be built into automated workflows. These check whether patches are likely to be relatively benign or risky.
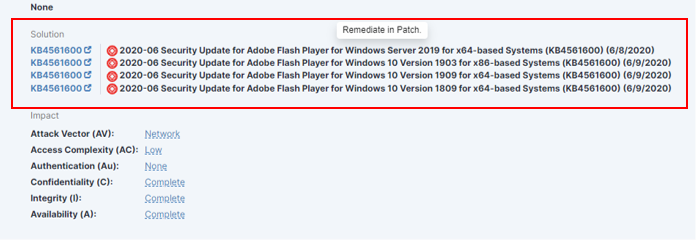
Remediation solutions readily available for action
3. Track your remediation cadence over time
Understanding both the speed and success of your remediation program is a key to understanding the effectiveness of your vulnerability and configuration management efforts. At the Verify phase, you not only need to validate whether the required changes have been made but also evaluate metrics to your performance.
In this way, you can see how quickly you can identify issues, how fast your team addresses them once discovered, whether service-level agreements (SLAs) are being met and how this compares to peer performance. Data like this will help to make this stage of the lifecycle more comprehensive and drive a Kaizen culture of continuous improvement.
4. Automate everywhere you can
In an ideal world, you would automate the entire vulnerability and configuration management lifecycle from Discover to Verify. This will reduce manual error and cyber risk, accelerate time-to-remediation and free up staff to work on other tasks. But in practice there are still elements that some organizations may wish to, or be required to, perform review, approval, audit, and validation of activities directly.
These include the initial asset valuation piece, which can be more art than science, and analysis of metrics in the Verify phase. Still, the quality of intelligence built into modern tools may surprise you — it’s always worth evaluating from time to time whether you could be automating more.
5. Start small to overcome resistance to change
One of the biggest barriers to modernizing vulnerability and configuration management programs is people and culture. There may be staff members in your team who are firmly against automatic remediations after having accidentally caused a production outage in the past through automated patching. There may be others who fear their jobs will be at risk if machines are used to fix endpoint problems. Some might simply complain that “this isn’t how things are done here.”
We all know change can be frightening for some people. But it’s also essential to drive continuous improvement. Consider tackling the low-hanging fruit first. This will show reluctant stakeholders the value of automated approaches to vulnerability and configuration management and how much more productive it can make them.
Try something fairly innocuous to start, such as automating the Discover to Assess phases of the lifecycle. An automatic scan triggered after discovering a new asset could reduce a process that took five days to just five minutes. On the remediation front, consider implementing automated patching or software updates for medium- or lower-severity issues in your non-production environments to demonstrate the speed and effectiveness before moving on to production environments.
6. Everything starts with policy
As important as technology is to enhancing vulnerability and configuration management, let’s not forget the basics. It all begins with drawing up the right policies, plans and SLAs. It could be something as simple as: “We’re going to develop a vulnerability management lifecycle that we define, and here are the SLAs for each cycle period.” Once those SLAs are in place, it may become clear that automated tools are the best way to achieve these goals.
7. Scan continuously for holistic risk reduction
Too often, organizations focus on meeting the bare minimum of compliance requirements without seeing the bigger picture — that effective vulnerability and configuration management is fundamentally good for business. It’s important, therefore, to ensure endpoint scans are not carried out simply to check the right regulatory boxes but as part of a holistic risk management strategy.
That means running scans continuously to identify, prioritize, and address problems as they appear rather than just before an audit. Remember to cover the entire IT environment — not just fixed assets but also custom code in development. Recent events have shown that supply chain attacks at this layer could have far-reaching consequences.
To learn more, check out the blog post 9 Ways Tanium Improves Vulnerability and Configuration Management.
If you’re ready to see it in action, sign up for a demo today.




